The current $1.5 billion Bybit hack turned North Korean Lazarus Group into one of many high 15 Ethereum holders on the planet. The breach despatched shockwaves by the crypto area, alerting customers who beforehand thought Ethereum was among the many most secure and most decentralized networks.
In a dialog with BeInCrypto, representatives from Holonym, Cartesi, and Komodo Platform mentioned the implications of this breach, steps to curb comparable conditions sooner or later, and the way public belief in Ethereum will be restored.
A Completely different Type of Breach
The Bybit hack shook the crypto group not simply due to the amount of funds stolen but additionally due to the character of the breach.
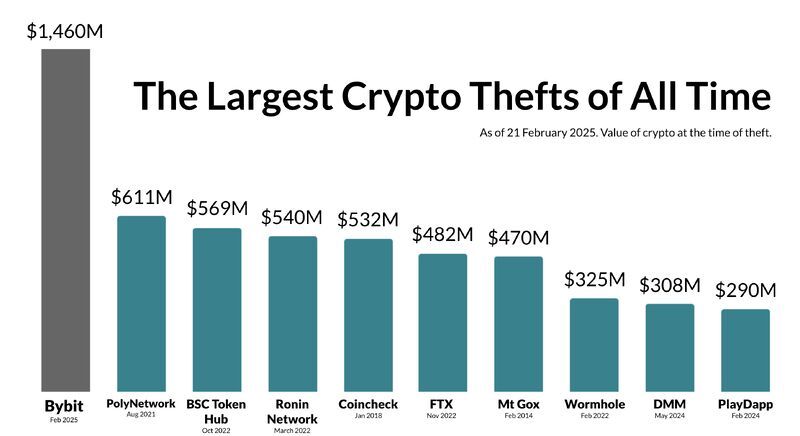
Whereas different crypto change breaches, just like the 2014 Mt. Gox episode or the 2018 Coincheck hack, concerned non-public keys or direct compromises of change wallets, Bybit’s scenario was totally different.
Reasonably than stealing non-public keys, the hackers manipulated the transaction signing course of, indicating that it was an infrastructure-level assault. The transaction signing course of was focused as an alternative of the asset storage itself.
Forensic evaluation of the Bybit hack traced the breach to Protected Pockets, a multi-signature pockets infrastructure offered by a 3rd social gathering. Protected Pockets makes use of sensible contracts and cloud-stored JavaScript recordsdata on AWS S3 to course of and safe transactions.
Hackers may secretly modify transactions by injecting malicious JavaScript into Protected Pockets’s AWS S3 storage. Due to this fact, though Bybit’s system was indirectly hacked, the hackers altered the vacation spot of transfers that Bybit had accepted.
This element uncovered a critical safety flaw. Third-party integrations grow to be weak factors even when an change locks down its methods.
Lazarus Group Amongst Ethereum’s Prime Holders
Following the monumental hack, North Korea is amongst the high 15 largest Ethereum holders.
In accordance to on-chain information, Gemini, which beforehand held the fifteenth place, holds 369,498 ETH in its Ethereum pockets. Since Bybit hackers stole over 401,000 ETH, they now overtook Gemini in possession.

The truth that an notorious group like Lazarus, accountable for a number of high-profile hacks in the crypto sector, now holds such an necessary quantity of Ether raises a number of belief points. Whereas preliminary hypothesis pointed towards a weak point in Ethereum’s decentralized nature, Nanak Nihal Khalsa, Co-Founding father of Holonym, discards this declare.
On condition that Ethereum’s governance and consensus mechanisms depend on validators somewhat than token holders, the Lazarus Group holding such a considerable quantity of ETH doesn’t compromise the community’s general decentralization.
“Lazarus nonetheless owns lower than 1% of ETH in circulation, so I don’t see it as extremely related past easy optics. Whereas it’s lots of ETH, they nonetheless personal lower than 1%. I’m not anxious in any respect,” Khalsa informed BeInCrypto.
Kadan Stadelmann, Chief Expertise Officer at Komodo Platform, agreed, emphasizing that Ethereum’s infrastructure design is the supply of its weak point.
“It proves a vulnerability in Ethereum’s structure: illicit actors may develop their holdings additional by concentrating on exchanges or DeFi protocols, and thus wield an affect over market dynamics and presumably change governance selections in Ethereum’s off-chain processes by voting on enchancment proposals. Whereas Ethereum’s technical decentralization has not been compromised, Lazarus Group has eroded belief in Ethereum,” Stadelmann informed BeInCrypto.
Nonetheless, whereas token holders can not affect Ethereum’s consensus mechanisms, they’ll manipulate markets.
Potential Impacts and Market Manipulations
Although the Bybit hackers have already completed laundering the stolen ETH, Stadelmann outlined a collection of doable eventualities that the Lazarus Group may have carried out with the large wealth they initially gathered. One choice is staking.
“Ethereum’s Proof-of-Stake safety depends on trustworthy validators and resilience of wallets, exchanges, and dApps. Whereas the Lazarus Group’s haul doesn’t threaten the blockchain’s consensus mechanism, since their holdings will not be recognized to be staked, it definitely raises the spectre that this could possibly be achieved. They’re unlikely to do that, because the funds they’ve stolen have been tracked,” he defined.
Alongside equally unlikely traces, the Bybit hackers may trigger a big market downturn by promoting their holdings altogether.
“Their holdings do give them a chance to control markets, reminiscent of in the event that they dump their holdings. This is able to be tough to do since their ETH are flagged. In the event that they attempt to change the ETH through promoting, their property could possibly be frozen,” Stadelmann added.
What Stadelmann is most anxious about wanting towards the long run is the affect hacks can have on Ethereum’s Layer 2 protocols.
“Lazarus and its companions may try and assault Layer 2 protocols like Arbitrum and Optimism. A censorship assault on layer 2 may undermine dApps and trigger the ecosystem to maneuver in direction of centralized transaction sequencers. That may underscore Ethereum’s weak point,” he stated.
Whereas Ethereum’s community was not compromised, Protected Pockets’s assaults underscored the vulnerabilities within the safety of the higher ecosystem.
“The breach has definitely elevated tensions within the ecosystem, and created an uneven token distribution. The query stays: will Lazarus or different hacking teams related to state actors try to use the Ethereum ecosystem, notably at layer 2?” Stadelmann concluded.
It additionally raised questions concerning the want for higher safety requirements.
Verification Over Belief
Khalsa argued that the Bybit hack, whereas not a risk to Ethereum’s core safety, highlighted the necessity for improved safety requirements amongst customers.
“Saying the hack is Ethereum’s downside is like saying loss of life by automobile accident is the automobile’s downside when the motive force didn’t put on a seatbelt. Might the automobile have extra security measures? Sure, and it ought to. However as a seatbelt has little to do with the automobile, the hack had little to do with Ethereum. It’s a protocol and it labored precisely as meant. The issue is the shortage of comfort and know-how for securely custodying digital property,” he stated.
Particularly, the incident uncovered vulnerabilities inside multi-signature wallets, demonstrating that reliance on third-party integrations can introduce important dangers, even with sturdy inner safety. In the end, even probably the most subtle pockets safety measures grow to be ineffective if the signing course of will be compromised.
Khalsa emphasised that confirmed self-custody safety measures exist, whereas multi-signature wallets will not be amongst them. He added that authorities businesses ought to have way back advocated for superior safety requirements and practices.
“The repercussion we are able to all hope for is getting critical about stopping North Korea from stealing extra funds. Whereas it’s not the federal government’s place to vary how self-custody is carried out, it’s completely the federal government’s place to encourage higher trade ‘greatest practices.’ This assault was because of the fable that multisigs of {hardware} wallets are safe. Sadly it took this assault for it to be acknowledged, however higher requirements set by authorities businesses may encourage safer practices with out the necessity for $1.5 billion compromises to get up the trade,” he asserted.
The incident additionally uncovered the necessity to confirm transactions somewhat than belief third-party functions.
A Resolution to Entrance-Finish Vulnerabilities
By injecting malicious JavaScript into weak Protected Pockets cloud servers, the Lazarus Group launched a classy assault, enabling them to imitate the interface and trick customers.
Based on Erick de Moura, co-founder of Cartesi, this exploit highlights a crucial vulnerability. The difficulty lies within the reliance on centralized construct and deployment pipelines inside a system meant for decentralization.
“The SAFE incident serves as a stark reminder that Web3 is just as safe as its weakest hyperlink. If customers can not confirm that the interface they work together with is real, decentralization turns into meaningless,” he stated.
De Moura additionally added {that a} widespread false impression in Web3 safety is that sensible contract breaches are among the many handiest types of hacking exchanges. Nonetheless, he deems that the Lazarus Group’s technique on Bybit proves in any other case. Injecting malicious code into the front-end or different off-chain elements is rather more seamless.
“The hackers didn’t have to breach sensible contracts or manipulate ByBit’s methods straight. As a substitute, they injected malicious code into the front-end interface, deceiving customers into considering they had been participating with a trusted platform,” he defined.
Regardless of these vulnerabilities, a transition from trust-based to verifiable safety is feasible.
The Case for Reproducible Builds
De Moura views the Bybit hack as a wake-up name for the Web3 group. As exchanges and builders reassess their safety, he argues that verifiable, reproducible builds are important to forestall future assaults.
“At its core, a reproducible construct ensures that when supply code is compiled, it all the time produces the identical binary output. This ensures that the software program customers work together with hasn’t been altered by a 3rd social gathering someplace within the deployment pipeline,” he stated.
Blockchain expertise is important to make sure that this course of takes place.
“Think about a system the place each software program construct generates binaries and sources in a verifiable means, with their fingerprints (or checksums) saved on-chain. As a substitute of working such builds on cloud servers or computer systems which might be vulnerable to safety breaches, they are often executed on devoted blockchain co-processors or decentralized computational oracles,” De Moura informed BeInCrypto.
Customers can examine the checksum of the front-end sources they’re loading in opposition to on-chain information by a browser plugin or function. A profitable match signifies an genuine construct interface, whereas a discrepancy indicators a possible compromise.
“If a verifiable reproducible builds strategy had been utilized to SAFE, the exploit may have been prevented. The malicious front-end would have failed verification in opposition to the on-chain report, instantly exposing the assault,” De Moura concluded.
This strategy presents a useful various to counting on customers with various ranges of self-custody information.
Addressing Gaps in Person Information
As assaults develop extra subtle, the shortage of person information about methods to securely custody digital property presents a big vulnerability.
The Bybit hack pissed off customers who initially thought that reliance on third-party integrations can be sufficient to safeguard their property. It additionally affected the broader notion of cryptocurrency safety.
“It reveals crypto continues to be within the Wild West and in its rising section when it comes to safety. I believe in a pair years we can have superior safety however in its present state, the general public concern is well-justified,” Khalsa stated.
In the end, embracing totally different approaches shall be important for the Web3 group to construct a safer and resilient ecosystem. A great start line is to demand higher trade practices and consider the mixing of verifiable, reproducible builds.
Disclaimer
Following the Belief Challenge tips, this function article presents opinions and views from trade consultants or people. BeInCrypto is devoted to clear reporting, however the views expressed on this article don’t essentially mirror these of BeInCrypto or its employees. Readers ought to confirm data independently and seek the advice of with knowledgeable earlier than making selections based mostly on this content material. Please notice that our Phrases and Situations, Privateness Coverage, and Disclaimers have been up to date.
