Ethereum’s not too long ago launched good pockets function, EIP-7702, is below scrutiny after blockchain safety researchers uncovered cybercriminals’ misuse of it. Following the Pectra improve, a number of pockets suppliers have begun integrating EIP-7702 options.
Analysts at Wintermute, a crypto buying and selling agency, famous that attackers used 97% of EIP-7702 pockets delegations to deploy contracts designed to empty funds from unsuspecting customers.
Hackers Use Ethereum’s EIP-7702 to Automate Mass Pockets Drainings
EIP-7702 quickly permits externally owned accounts (EOAs) to function as good contract wallets. The improve permits options like transaction batching, spending limits, passkey integration, and pockets restoration—all with out altering pockets addresses.
Whereas these upgrades intention to reinforce usability, malicious actors are leveraging the usual to hurry up fund extractions.
As an alternative of shifting ETH manually from every compromised pockets, attackers now authorize contracts that routinely ahead any acquired ETH to their very own addresses.
“Little doubt attackers are one of many early adopters of latest capabilities. 7702 was by no means meant to be a silver bullet and it does have nice use circumstances,” Rahul Rumalla, Chief Product Officer at Protected, mentioned.
Wintermute’s evaluation exhibits that the majority of those pockets delegations level to equivalent codebases designed to “sweep” ETH from compromised wallets.
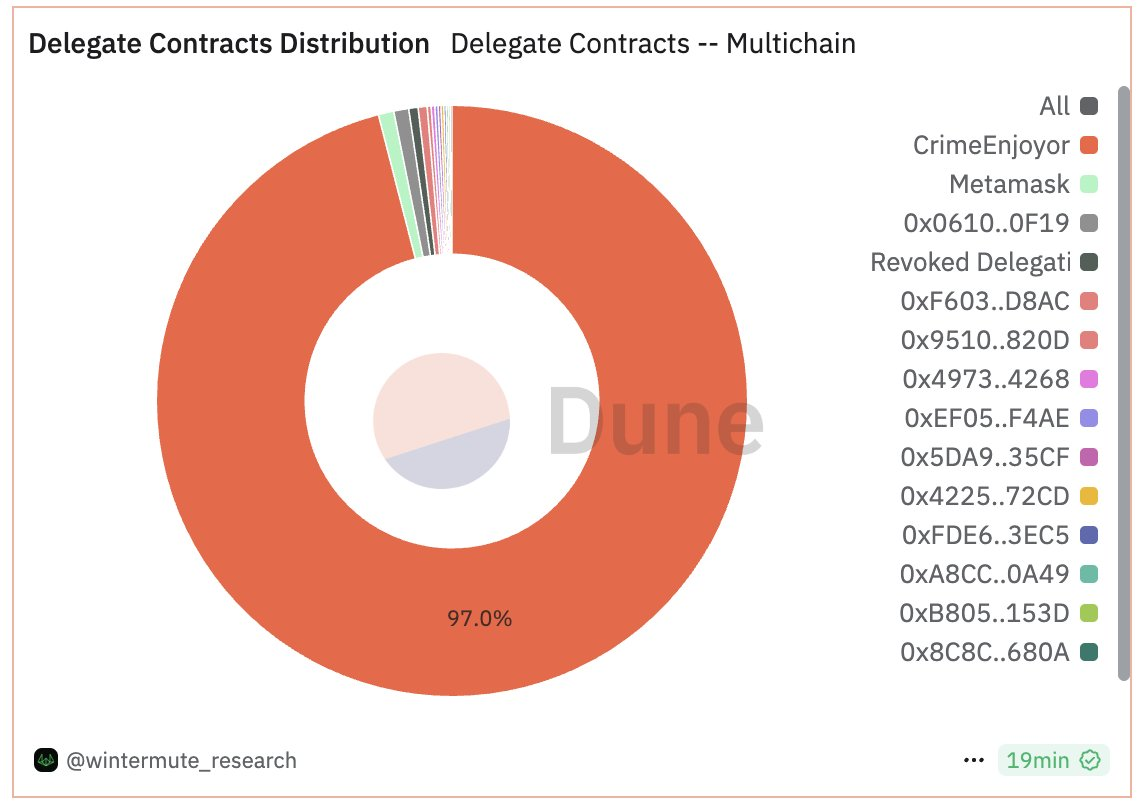
These sweepers routinely switch any incoming funds to attacker-controlled addresses. Out of practically 190,000 delegated contracts examined, greater than 105,000 had been linked to illicit exercise.
Koffi, a senior knowledge analyst at Base Community, defined that over 1,000,000 wallets interacted with suspicious contracts final weekend.
He clarified that attackers didn’t use EIP-7702 to hack the wallets however to streamline theft from wallets with already uncovered personal keys
The analyst furthered that one standout implementation features a obtain perform that triggers ETH transfers the second funds land within the pockets, eliminating the necessity for guide withdrawal.
Yu Xian, founding father of blockchain safety agency SlowMist, confirmed that the perpetrators are organized theft teams, not typical phishing operators. He famous that EIP-7702’s automation capabilities make it notably engaging for large-scale exploits.
“The brand new mechanism EIP-7702 is used most by coin stealing teams (not phishing teams) to routinely switch funds from pockets addresses with leaked personal keys/mnemonics,” he said.
Regardless of the size of the operation, there are not any confirmed earnings up to now.
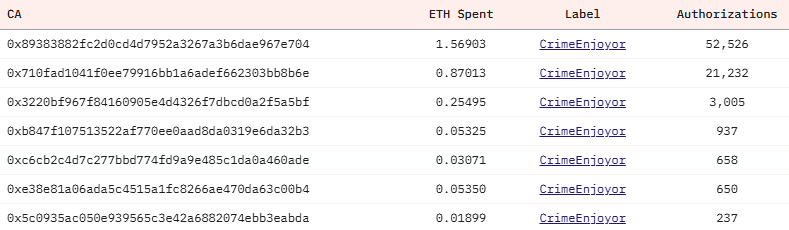
A researcher at Wintermute famous that attackers have spent about 2.88 ETH authorizing over 79,000 addresses. One deal with alone executed practically 52,000 authorizations, but the goal deal with has not acquired any funds.
Disclaimer
In adherence to the Belief Venture tips, BeInCrypto is dedicated to unbiased, clear reporting. This information article goals to supply correct, well timed info. Nevertheless, readers are suggested to confirm info independently and seek the advice of with knowledgeable earlier than making any selections based mostly on this content material. Please be aware that our Phrases and Situations, Privateness Coverage, and Disclaimers have been up to date.
