Based on Cisco Talos, a North Korean‑aligned group has quietly stepped up efforts to focus on crypto job hunters in India with a brand new Python‑primarily based distant entry trojan.
The marketing campaign makes use of pretend job websites and staged interviews to trick candidates into working malicious code. Victims find yourself handing over keys to their wallets and password managers.
Bogus Job Platforms
Job seekers are lured by postings that mimic huge names like Coinbase, Robinhood and Uniswap. Recruiters attain out by means of LinkedIn or e mail. They invite candidates to a “ability‑testing” web site. It feels innocent at first. Behind the scenes, the positioning is amassing system particulars and browser data.
A pattern of a pretend job web site. Supply: Cisco Talos
Misleading Interview Course of
After the take a look at, candidates be part of a reside video interview. They’re advised to replace their digicam drivers. In a fast transfer, they copy and paste instructions right into a terminal window. One click on and PylangGhost is put in. The entire scheme runs easily—till the malware takes over.
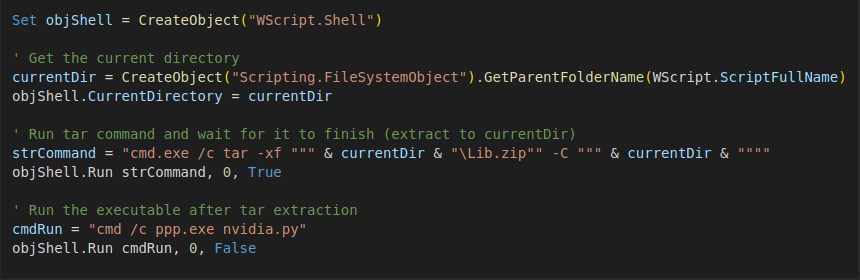
The primary stage merely unzips a Python distribution library and launches the RAT. Supply: Cisco Talos
Superior RAT Instrument
PylangGhost is a spin on the sooner GolangGhost software. As soon as energetic, it grabs cookies and passwords from greater than 80 browser extensions. This checklist consists of MetaMask, 1Password, NordPass, Phantom, Bitski, Initia, TronLink and MultiverseX.
The trojan then opens a again door for distant management. It might take screenshots, handle information, steal browser information and hold a hidden presence on the system.
Historical past Of Related Assaults
North Korean hackers used a pretend recruitment take a look at in April earlier than the $1.4 billion Bybit heist. They usually’ve tried comparable tips with contaminated PDFs and malicious hyperlinks.
This group—often known as Well-known Chollima or Wagemole—has stolen tens of millions by means of crypto pockets breaches since 2019. Their aim is easy: get legitimate credentials after which quietly transfer funds.
Trade Response Measures
Safety groups are on alert. They advocate checking each URL for spelling errors and odd domains. Specialists say to confirm job provides by means of trusted channels.
Endpoint detection instruments ought to flag any script that calls distant servers. And multi‑issue authentication can block stolen passwords from giving full entry.
This alert exhibits how far state‑linked actors will go to steal crypto belongings. The combo of social engineering and customized malware is a potent threat. Anybody trying to find work in blockchain ought to double‑test each hyperlink and by no means run unverified code.
Conserving {hardware} wallets offline and utilizing separate profiles for job looking can lower down on publicity. Vigilance within the hiring course of and stable technical controls stay the very best protection towards these evolving threats.
Featured picture from Shutterstock, chart from TradingView

Editorial Course of for bitcoinist is centered on delivering totally researched, correct, and unbiased content material. We uphold strict sourcing requirements, and every web page undergoes diligent evaluation by our staff of prime expertise consultants and seasoned editors. This course of ensures the integrity, relevance, and worth of our content material for our readers.