North Korea-linked hackers are ramping up assaults on the cryptocurrency sector, with current investigations pointing to the Lazarus Group’s evolving strategies.
On-chain analyst ZachXBT has revealed a string of incidents tied to the regime’s cyber operations. These incidents embody using pretend developer profiles and sophisticated laundering methods.
Lazarus Hackers Steal Thousands and thousands as North Korea Intensifies Crypto Assaults
On June 29, Zachxbt reported that the Lazarus Group scammed a person out of $3.2 million in digital property on Might 16.
The stolen funds had been rapidly transformed from Solana to Ethereum. The hacker then deposited 800 ETH into Twister Money, a privateness protocol that obscures cryptocurrency transactions.
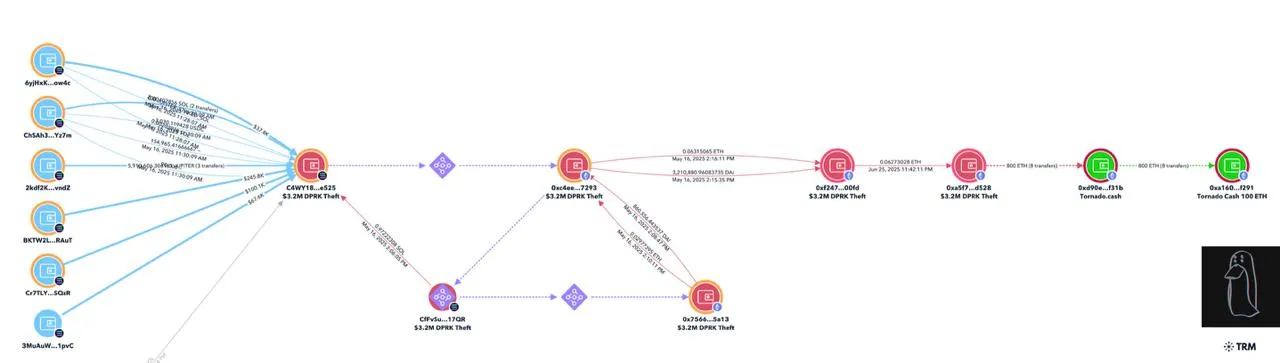
On the time of reporting, an estimated $1.25 million stays in an Ethereum pockets holding DAI and ETH.
In the meantime, this assault is only one in a sequence of actions by the Lazarus Group, which more and more targets high-value crypto property.
On June 27, ZachXBT linked the group to a major exploit affecting a number of NFT tasks related to Matt Furie, the creator of Pepe. The assault additionally impacted tasks like ChainSaw and Favrr.
This sequence of assaults, which started on June 18, allowed the hackers to take management of a number of NFT contracts. They then minted and dumped NFTs, stealing an estimated $1 million from these tasks.
ZachXBT’s investigation revealed that the hackers moved the stolen funds throughout three wallets. Ultimately, they transformed a number of the ETH into stablecoins and transferred them to MEXC, a centralized trade.
In the meantime, the sample of stablecoin transfers, tied to a selected MEXC deposit handle, means that the attackers engaged in a number of crypto tasks.
Furthermore, the evaluation uncovered hyperlinks to GitHub accounts with Korean language settings and time zones in line with North Korean exercise.
“Different indicators revealed from inner logs level out irregularities in a suspected DPRK IT staff resume. Why would a developer who claims to be dwelling within the US have a Korean language setting, Astral VPN utilization, and have an Asia/Russia time zone?,” ZachXBT questioned.
In Favrr’s case, investigators suspect the mission’s chief know-how officer, Alex Hong, of being a North Korean IT employee. ZachXBT additionally reported that Hong’s LinkedIn profile was not too long ago deleted, and his work historical past couldn’t be verified.
Certainly, these incidents spotlight North Korea’s ongoing position in cryptocurrency theft. Blockchain evaluation agency TRM Labs not too long ago linked the nation’s hackers to just about $1.6 billion in stolen funds, accounting for about 70% of all stolen crypto property this yr.
Disclaimer
In adherence to the Belief Mission tips, BeInCrypto is dedicated to unbiased, clear reporting. This information article goals to supply correct, well timed info. Nonetheless, readers are suggested to confirm info independently and seek the advice of with knowledgeable earlier than making any selections based mostly on this content material. Please notice that our Phrases and Situations, Privateness Coverage, and Disclaimers have been up to date.
