Anonymity is the tip purpose when learning privateness, and it’s helpful to consider de-anonymization as a recreation.
We think about an adversary with some entry to info, and it tries to guess accurately who amongst a set of candidates was answerable for some occasion within the system. To defend in opposition to the adversary successful, we have to maintain it guessing, which may both imply limiting its entry to info or utilizing randomness to extend the quantity of knowledge it must succeed.
Many readers will likely be acquainted with the sport of “Guess Who?”. This recreation may very well be described as a turn-based composition of two cases of the extra common recreation “twenty questions.” In “twenty questions,” you secretly select a component from a given set, and your opponent tries to guess it accurately by asking you as much as 20 yes-or-no questions. In “Guess Who?” either side take turns taking part in in opposition to one another, and the primary to guess accurately wins. The set of components is mounted in “Guess Who?”, consisting of 24 cartoon characters with varied distinguishing options, equivalent to their hair shade or fashion. Every character has a singular title that unambiguously identifies them.
The solutions to a yes-or-no query could be represented as a bit — zero or one. Twenty bits can categorical, in base 2, any complete quantity within the vary 0 to 1,048,575, which is 2²⁰-1. If a set could be completely ordered, every component within the set could also be listed by its numbered place within the order, which uniquely identifies it. So, 20 bits can uniquely handle considered one of simply over 1,000,000 components.
Though 2²⁰ is the utmost variety of components of a set that may very well be uniquely recognized utilizing simply the solutions to twenty yes-or-no questions, in real-world conditions, 20 solutions will typically comprise much less info than that. For many units and combos of questions, issues will virtually definitely not line up completely, and never each query will bisect the candidate components independently of the opposite questions. The solutions to some questions is perhaps biased; some questions’ solutions may correlate with these of different questions.
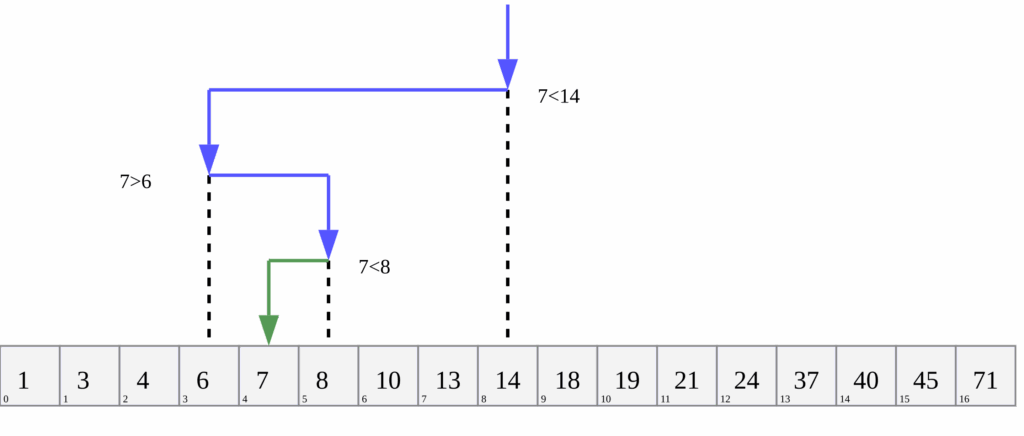
Suppose that as a substitute of asking one thing like “does your character have glasses?” you at all times ask, “Alphabetically, does your character’s title seem earlier than [median remaining character’s name]?”. It is a binary search, which is able to maximize how informative the reply to every query will likely be: At each step, the median title partitions the set of remaining characters, and the query eliminates one of many two halves. Repeatedly halving the remaining candidates will slim down the search as shortly as yes-or-no solutions make potential; solely a logarithmic variety of steps is required, which is far quicker than, say, a linear scan (i.e., checking one after the other: “Is it Alice? No? How about Bob? …”).
Keep in mind that in case you are taking part in to win, the purpose of the sport is to not get essentially the most info out of your opponent however to be the primary to guess accurately, and it seems that maximizing the knowledge per reply is definitely not the optimum technique — no less than when the sport is performed truthfully. Equally, when utilizing video games to check privateness, one should assume the adversary is rational in line with its preferences; it’s pretty straightforward to by accident optimize for a subtly incorrect end result, because the adversary is taking part in to win.
Lastly, suppose the gamers are not assumed to be sincere. It needs to be obvious that one can cheat with out getting detected; as a substitute of selecting a component of the set initially after which answering truthfully in response to each query, you may at all times give the reply that would go away the most important variety of remaining candidates. Adaptively chosen solutions can subsequently decrease the speed at which one’s opponent obtains helpful info to win the sport. On this so-called Byzantine setting, the optimum technique is not the identical as when gamers are sincere. Right here, an opponent’s greatest response could be to stay with binary search, which limits the benefit of taking part in adaptively.
Adaptive “Guess Who?” is fairly boring, much like how tic-tac-toe ought to at all times finish in a draw for those who’re paying consideration. To be exact, as we are going to see within the subsequent part, there are 4.58 bits of knowledge to extract out of your maximally adversarial opponent, and the foundations of the sport can be utilized to pressure the opponent to decide to these bits. This implies the primary participant can at all times win after 5 questions. The transcript of solutions in such video games ought to at all times include uniformly random bits, as anything would give an edge to at least one’s opponent. Sadly, privateness protections utilizing such adaptivity or added randomness are tough to construct and perceive, so precise privateness software program is often considerably more durable to investigate than these toy examples.
Measuring Anonymity: Shannon Entropy
The info content material of a solution in “Guess Who?” — often known as its Shannon entropy — quantifies how shocking it’s to be taught. For instance, for those who already came upon that your opponent’s character is bald, it gained’t shock you to be taught that they don’t have black hair; this reply incorporates no further info. This wasn’t shocking as a result of, earlier than being instructed, you can infer that the likelihood of getting black hair was zero.
Suppose that two choices stay from the set of candidates; it’s principally a coin toss, and both of the 2 choices needs to be equally seemingly and, subsequently, equally shocking. Studying that it’s choice A tells you it isn’t B — equivalently, studying that it’s not B tells you that it should be A — so just one yes-or-no query, one bit of knowledge, is required to take away all uncertainty.
This worth could be calculated from the likelihood distribution, which on this binary instance is Bernoulli with p=1/2.
First, compute the negation of the bottom 2 logarithm of the likelihood of every case, or equivalently invert the likelihood first and skip the negation:
First, compute the negation of the bottom 2 logarithm of the likelihood of every case, or equivalently invert the likelihood first and skip the negation:
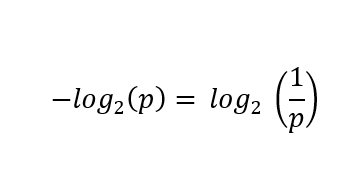
In each circumstances:
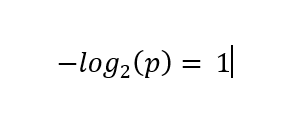
These values are then scaled by multiplying these values by their corresponding possibilities (as a kind of weighted common), leading to a contribution of ½ bits for both case. The sum of those phrases, 1 on this case, is the Shannon entropy of the distribution.
This additionally works with greater than two outcomes. For those who begin the sport by asking, “Is it [a random character’s name]?” you’ll most definitely solely be taught
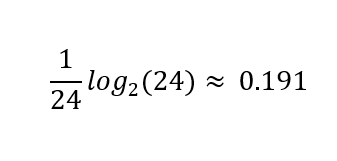
bits of knowledge if the reply was “no.”
At that time log₂(23) ≈ 4.52 bits quantify your remaining uncertainty over the 23 equally seemingly remaining prospects. Then again, for those who had been fortunate and guessed accurately, you’ll be taught the complete log₂(24) ≈ 4.58 bits of knowledge, as a result of no uncertainty will stay.
Just below 5 bits are wanted to slim right down to considered one of 24 characters. Ten bits can establish one in 1,024; 20 bits, round one in 1,000,000.
Shannon entropy is common sufficient to quantify non-uniform distributions, too. Not all names are equally in style, so an fascinating query is, “How a lot entropy is in a reputation“? The linked submit estimates this at roughly 15 bits for U.S. surnames. In line with one other paper, first names within the U.S. comprise roughly 10-11 bits. These estimates suggest an higher sure of 26 bits per full title, however keep in mind that a typical title like John Smith will comprise much less info than an unusual one. (Uniquely addressing the whole U.S. inhabitants requires 29 bits.)
As of writing, the world inhabitants is slowly however certainly approaching 8.5 billion, or 2³³ folks. Thirty-three is just not a really massive quantity: What number of bits are in a birthdate? Simply an age? Somebody’s metropolis of residence? An IP handle? A favourite film? A browser’s canvas implementation? A ZIP code? The phrases of their vocabulary, or the idiosyncrasies of their punctuation?
These are tough questions. Not like these video games and fashionable cryptography, the place secrets and techniques are random and preferentially ephemeral, we will’t randomize, expire or rotate our real-life figuring out attributes.
Moreover, this personally figuring out info typically leaks each by necessity and generally unnecessarily and unintentionally all through our lives. We frequently must belief folks with whom we work together to not reveal this info, whether or not by sharing it with third events or by accident leaking it. Maybe it’s not in contrast to how we should belief others with our lives, like docs or skilled drivers and pilots. Nonetheless, definitely it isn’t comparable when it comes to how obligatory it’s to belief as a matter after all in relation to our private knowledge.
An Entropist Perspective on Anonymity
Privateness-enhanced techniques enable customers to disguise in a crowd. For instance, for those who observe a connection to your server from a Tor exit node, for all you already know, it’s considered one of probably 1000’s of Tor customers that established that connection. Informally, given some occasion {that a} deanonymization adversary has noticed — maybe by intercepting a message being transmitted between two nodes in a community — a selected consumer’s anonymity set refers back to the set of potential customers to whom that occasion is perhaps attributed.
If the receiver of an nameless message is taken to be the adversary, then their greatest guess from a set of candidate senders is the sender’s anonymity set. If this hypothetical system is absolutely nameless, then any consumer is equally prone to have despatched the message, aside from the receiver.
Two influential papers that proposed to measure anonymity when it comes to the entropy of the anonymity set had been printed concurrently: “In the direction of Measuring Anonymity” by Claudia Díaz, Stefaan Seys, Joris Claessens and Bart Preneel, and “In the direction of an Data Theoretic Metric for Anonymity” by Andrei Serjantov and George Danezis. These works generalize from the idea that the adversary can guess the right consumer from an anonymity set no higher than probability, to a mannequin that accounts for nonuniform likelihood distributions over this set. Each suggest the quantification of anonymity set sizes when it comes to bits of entropy.
When the anonymity set is completely symmetric, solely the uniform distribution is sensible, so changing the anonymity set dimension to bits is only a matter of computing a log₂(n) the place n is the scale of the set. For instance, 1024 equiprobable components in a set have 10 bits of entropy of their distribution.
When the distribution is just not uniform, the entropy of the distribution decreases. For instance, if both heads or tails is feasible, however there’s a ¼ likelihood of heads, ¾ of tails, the overall entropy of this distribution is simply
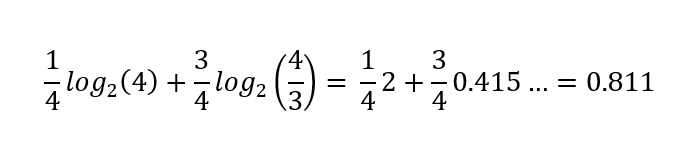
bits as a substitute of a full bit. This quantifies the uncertainty represented in a likelihood distribution; the result of flipping this bent coin is relatively much less unsure than that of a good coin.
Shannon entropy is a particular case of a complete household of entropy definitions. It characterizes the typical info content material in a message (a yes-or-no reply, or extra typically) drawn from a likelihood distribution over potential messages. A extra conservative estimate may use min-entropy, which considers solely the best likelihood component as a substitute of calculating the arithmetic imply, quantifying the worst-case situation. On this submit, we’ll persist with Shannon entropy. For a extra in-depth dialogue and a nuanced interpretation of the entropist perspective, Paul Syverson’s “Why I’m not an Entropist” is a considerate learn.
Anonymity Intersections
In k-anonymity: a mannequin for safeguarding privateness, Latanya Sweeney critiques a few of her prior outcomes as motivation — outcomes which demonstrated re-identification of “anonymized” knowledge. Individually, every attribute in an information set related to an entry, equivalent to a date of delivery, may appear to disclose little or no concerning the topic of that entry. However just like the yes-or-no questions from the sport, solely a logarithmic quantity of knowledge is required; in different phrases, combos of surprisingly small numbers of attributes will typically be adequate for re-identification:
For instance, a discovering in that examine was that 87% (216 million of 248 million) of the inhabitants in the USA had reported traits that seemingly made them distinctive primarily based solely on {5-digit ZIP, gender, date of delivery}. Clearly, knowledge launched containing such details about these people shouldn’t be thought of nameless.
As a tough estimate, a string of 5 digits would have log₂(10⁵) ≈ 16.6 bits of max entropy, however there are fewer ZIP codes than that, log₂(4.3 x 10⁴) ≈ 15.4 — and needless to say the inhabitants is just not uniformly distributed over ZIP codes, so 13.8 could be a higher estimate. A gender area would often comprise barely greater than 1 bit of knowledge in most circumstances, as a result of even when nonbinary genders are represented, the vast majority of entries will likely be male or feminine. That stated, entries with nonbinary values would reveal much more than 1 bit concerning the topic of that entry. A date of delivery can be tough to estimate with out wanting on the distribution of ages.
Ignoring February 29 and assuming uniformly distributed birthdays and 2-digit delivery yr, the entropy could be log₂(365 x 10²) ≈ 15.1. Once more, a extra reasonable estimate is on the market, 14.9 bits. Taken collectively, the extra conservative estimates complete roughly 29.7 bits. For comparability, the entropy of a uniform distribution over the U.S. inhabitants on the time is log₂(248 x 10⁶) ≈ 27.9 bits, or log₂(342 x 10⁶) ≈ 28.4 with up-to-date figures.
The next diagram from the paper will in all probability look acquainted to anybody who has spent a while studying what an “internal be a part of” is in SQL. It illustrates a special instance the place Sweeney linked medical data to the voter registration checklist utilizing the identical fields, figuring out then-Massachusetts Governor William Weld’s particular file in an “anonymized” medical dataset:
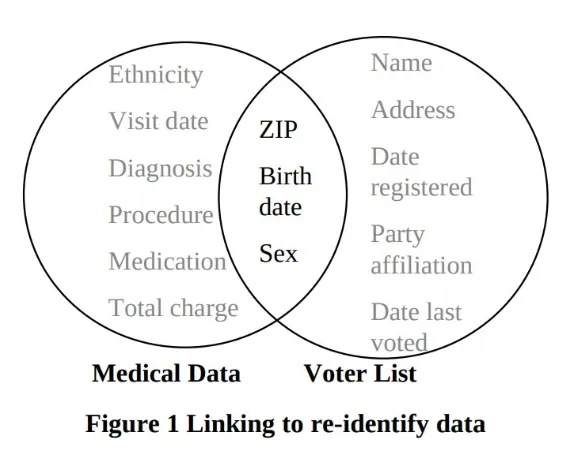
This sort of Venn diagram, with two units represented by two overlapping circles and the overlapping half highlighted, sometimes represents an intersection between two units. Units are unordered collections of components, equivalent to rows in a database, numbers, or anything that may be mathematically outlined. The intersection of two units is the set of components which can be current in each units. So, for instance, throughout the voter registration checklist, we would speak concerning the subset of all entries whose ZIP code is 12345, and the set of all entries whose delivery date is January 1, 1970. The intersection of those two subsets is the subset of entries whose ZIP code is 12345 and whose date of delivery is January 1, 1970. Within the governor’s case, there was only one entry within the subset of entries whose attribute values matched his attributes within the voter registration checklist.
For knowledge units with totally different buildings, there’s a small complication: If we consider them as units of rows, then their intersection would at all times be empty, as a result of the rows would have totally different shapes. When computing the internal be a part of of two database tables, solely the values of columns which can be current in each tables are in some sense intersected by specifying one thing like JOIN ON a.zip = b.zip AND a.dob = a.dob, or the much less moveable USING(zip, dob) syntax, however these intersecting values are associated to the rows they got here from, so the general construction of linking two knowledge units is a little more concerned.
Be aware that Sweeney’s diagram depicts the intersection of the columns of the information units, emphasizing the extra main drawback, which is that attributes included within the “anonymized” knowledge set unintentionally had a non-empty intersection with the attributes of different publicly out there knowledge units.
On the utilized facet of the k-anonymity mannequin, the procedures for anonymizing datasets described within the paper have fallen out of favor on account of some weaknesses found in subsequent work (“Assaults on Deidentification’s Defenses” by Aloni Cohen). That central concept in k-anonymity is to make sure that for each potential mixture of attributes, there are no less than okay rows containing each particular mixture within the knowledge, which suggests log₂(okay) further bits of knowledge could be wanted to establish an entry from its congruent ones. The deidentification process urged for guaranteeing this was the case was to redact or generalize in a data-dependent manner, for instance, drop the day from a date of delivery, conserving the yr and month, and even solely the yr, if that’s not sufficient. Cohen’s work exhibits how straightforward it’s to underestimate the brittleness of privateness, as a result of even discarding info till there’s okay of each mixture, the redaction course of itself leaks details about the statistics of the unredacted knowledge set. Such leaks, even when very refined, won’t solely add up over time, however they may sometimes compound. Accounting for privateness loss utilizing bits, that are a logarithmic scale, maybe helps present a greater instinct for the sometimes exponential fee of decay of privateness.
Anonymity in Bitcoin CoinJoins: Intersection Assaults
Of their paper “When the Cookie Meets the Blockchain: Privateness Dangers of Net Funds by way of Cryptocurrencies,” Steven Goldfeder, Harry Kalodner, Dillon Reisman and Arvind Narayanan describe two unbiased however associated assaults. Maybe extra importantly, additionally they make a really compelling case for the brittleness of privateness extra broadly, by clearly demonstrating how privateness leaks can compound.
In Bitcoin, a pure definition of an anonymity set for a coin is the set of pockets clusters into which the coin may plausibly be merged. The anonymity set is nontrivial if there may be a couple of candidate cluster, through which case merging could be contingent on acquiring further info. New transactions may introduce uncertainty, necessitating the creation of recent clusters for outputs that may’t be merged into any present cluster (but). Then again, new transactions and out-of-band info also can take away uncertainty and facilitate the merging of clusters. Mostly, if the multi-input heuristic is taken into account legitimate for such a brand new transaction, then the clusters of the enter cash will likely be merged. Nevertheless, as we noticed earlier than, many heuristics exist, a few of that are alarmingly correct.
Suppose that Alice obtained some bitcoin right into a pockets below her management. Some may need been withdrawn from an change (presumably with KYC info). Possibly a good friend paid her again for lunch. Possibly she offered her automotive. After making a number of transactions, Alice realizes that her transaction historical past is seen to all and fairly simple to interpret, however quickly she might want to make not only one, however two separate transactions, with stronger privateness assurances than she has been counting on to this point.
After studying a bit about privateness, Alice decides to make use of a pockets that helps CoinJoin. Over a number of CoinJoin transactions, she spends her present cash, acquiring alternative cash that apparently have a non-trivial anonymity set. Earlier than CoinJoining, her pockets was seemingly clusterable. After CoinJoining, every UTXO she now has can’t be assigned to any particular cluster, since different customers’ pockets clusters are additionally implied within the varied CoinJoin transactions.
The instinct behind CoinJoin privateness is that since a number of inputs belonging to totally different customers are used to create outputs that every one look the identical, nobody output could be linked to a particular enter. That is considerably analogous to a mixnet, the place every CoinJoin transaction is a relay and the “messages” being blended are the cash themselves. This analogy could be very simplistic, there are a lot of problems when implementing CoinJoins that trigger it to interrupt down, however we are going to ignore these nuances on this submit and provides Alice’s chosen CoinJoin pockets the advantage of the doubt and assume that Alice can at all times efficiently spend only one enter into every CoinJoin, and that this ends in excellent mixing of her funds with these of the opposite events to the CoinJoin. Beneath these assumptions, if there are okay equal outputs in a CoinJoin transaction, and okay separate clusters for the inputs, then every output’s anonymity set ought to have log₂(okay) bits of entropy when this transaction is created.
Publish-CoinJoin Clustering
The stage is now set for the primary assault described within the paper. This assault was made potential by inclusion of third celebration sources, e.g., a cost processor’s javascript on service provider web sites. Supposing the cost handle used for the transaction is revealed to the third celebration, that might hyperlink Alice’s net session to her on-chain transaction. The paper is from 2017, so the specifics of web-related leaks are considerably dated by now, however the precept underlying this concern is as related as ever.
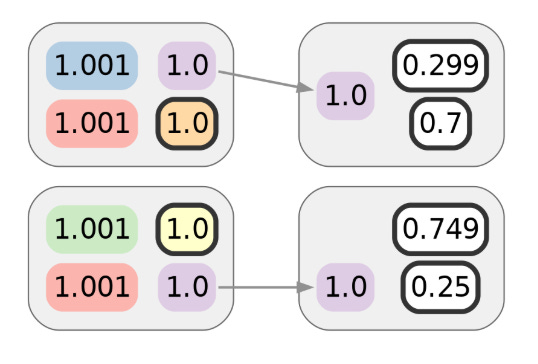
Alice makes use of considered one of her CoinJoin UTXOs to make the primary of these privacy-demanding transactions. Assuming no semantic leaks (equivalent to a billing handle associated to a purchase order) or metadata leaks (maybe she broadcasts utilizing Tor), this transaction ought to protect the privateness Alice obtained from the prior CoinJoin transaction. As drawn right here, that might be 1 bit’s price. The colours of inputs or outputs point out the cluster they’re already assigned to. Alice’s cash are in pink, and gradients characterize ambiguity:
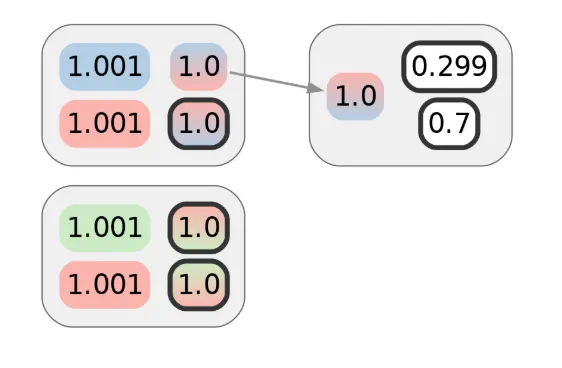
Whereas the primary transaction doesn’t reveal a lot by itself, suppose Alice makes one other transaction. Let’s say it’s with a special service provider, however one which makes use of the identical cost processor as the primary service provider. Naively, it might seem that the next diagram represents the privateness of Alice’s cost transactions, and that the adversary would want 2 bits of further info — 1 for every transaction — to attribute them each to Alice’s cluster:
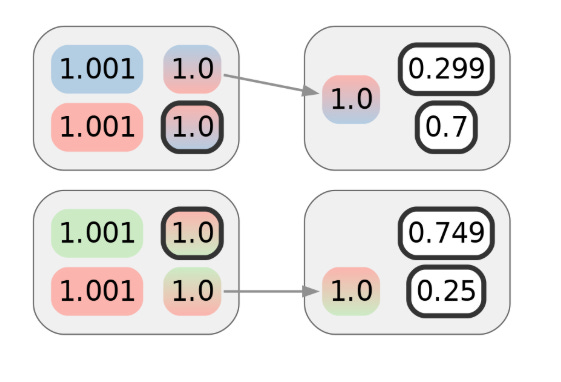
Though Alice intends this to be unlinkable to the primary transaction, she won’t understand her net shopping exercise is being tracked. The paper confirmed that this sort of monitoring was not simply potential however even sensible, and might divulge to a 3rd celebration that the 2 transactions could be clustered despite the fact that they don’t seem associated on-chain. Visually, we will characterize this clustering with further colours:
Net monitoring, as mentioned within the paper, is only one of some ways info that facilitates clustering can leak. For instance, web site breaches can lead to buy data being made public, even years after the very fact. In no less than one instance, authorized proceedings, that are supposed to guard victims, ended up exposing them to much more hurt by needlessly revealing details about the on-chain transactions of shoppers by way of improper redaction of the transacted quantities. The earlier submit on the historical past of pockets clustering gives a number of further examples.
Particularly within the context of CoinJoins, a typical manner that this kind of linkage may happen is when the change outputs of post-mix cost transactions are subsequently CoinJoined in a way that causes them to be linkable by clustering the inputs. That is often known as the poisonous change drawback, which is illustrated within the subsequent diagram. Be aware that white doesn’t characterize a single cluster, simply lack of clustering info on this instance.
If the coordinator of the supposedly “trustless” CoinJoin protocols is malicious, then even trying to CoinJoin might hyperlink the transactions, even when this doesn’t grow to be self-evident on-chain. The results are the identical because the assault described within the paper, besides {that a} CoinJoin coordinator also can fake that some members did not submit their signatures in time, actively however covertly, or no less than deniably disrupting rounds to acquire extra clustering info.
Intersection Antecessor Clusters
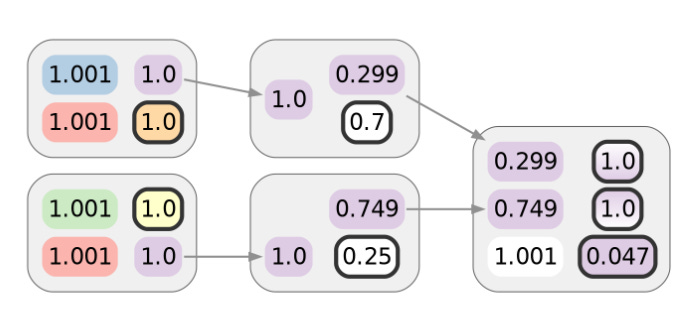
Sadly for Alice, the story doesn’t finish there. What the paper confirmed subsequent was that given such linking of post-CoinJoin transactions, no matter how this clustering was discovered, an intersection assault on the privateness of the CoinJoin transactions themselves additionally turns into potential.
It’s as if the adversary is taking part in “Guess Who?” and is given a cost transaction, then tries to guess the place the funds originated from. Contemplate the set of inputs for every CoinJoin transaction. Each one of many spent cash is assigned to some cluster. Each one of many CoinJoin transactions Alice participated in has an enter that’s linkable to considered one of her clusters. The privateness of such transactions derives from being linked to numerous in any other case unrelated clusters. Armed with data that post-CoinJoin transactions hyperlink a number of CoinJoin outputs collectively, the adversary can compute the intersection of the units of related clusters. How typically will or not it’s the case {that a} random particular person consumer participated in each transaction that Alice did? What about a couple of? Not fairly often. And suppose the intersection incorporates a singular cluster, which may typically finally be the case. In that case, the adversary will be capable to hyperlink Alice’s transactions to one another and her pre-CoinJoin transaction historical past, successfully undoing the combination.
Visually, this combines the inferences of earlier diagrams. For every coin within the purple cluster of the final two diagrams, we will intersect the units of colours within the gradients depicted within the diagram earlier than that:

Solely Alice’s pink cluster is within the intersection, in order that the purple cluster could be merged into the pink one. Not solely do Alice’s clusters merge, since this instance solely has two consumer CoinJoin transactions, the remaining clusters can be merged with their ancestors by strategy of elimination, so Alice’s linkable funds would additionally probably deanonymize a hypothetical Bob and Carol on this explicit case:

This means that even when CoinJoins functioned like an ideal combine (which they don’t), inadequate post-mix transaction privateness can moreover undermine the privateness of the prior CoinJoin transactions, and way more quickly than appears intuitive. The graph construction, which connects Bitcoin transactions, incorporates a wealth of knowledge out there to a deanonymization adversary.
Privateness considerations are sometimes downplayed, maybe on account of defeatist attitudes in mild of the challenges of stopping and even controlling privateness leaks. Hopefully consciousness will enhance, and issues will play out like they did in cryptography in earlier many years — whether or not it’s not delivery weak “export” crypto, or how timing facet channels had been largely ignored at first, however are actually broadly understood to be virtually exploitable and implementations that don’t take them into consideration are thought of insecure. That stated, it’ll at all times be tougher: In cryptography, we’ve got extra alternatives to restrict the hurt of unintended publicity by preferring ephemeral keys over long-term ones, or no less than rotating long-term keys periodically. Sadly, the closest analog of rotating keys I can consider in privateness is witness safety packages — a somewhat excessive and expensive measure, and much from completely efficient.
For privateness in the actual world, the challenges of CoinJoin privateness stays.
That is an edited model of the article by @not_nothingmuch, posted on Spiral’s Substack June 11.
BM Large Reads are weekly, in-depth articles on some present matter related to Bitcoin and Bitcoiners. If you could have a submission you assume matches the mannequin, be happy to succeed in out at editor[at]bitcoinmagazine.com.
