Crypto safety consultants are the primary responders of the blockchain world, tracing stolen tens of millions throughout wallets, mixers and obscure bridges earlier than the path goes chilly.
They function in conflict rooms that type inside minutes of a breach, utilizing open-source intelligence, inside alert techniques and personal networks that span borders and languages.
When a significant hack breaks, the crypto group turns to its pseudonymous detectives, whose social accounts are sometimes the primary to translate blockchain trails.

What started as hobbyists decoding suspicious transactions has developed into a world net of digital sleuths who monitor the movement of stolen funds sooner than most authorities. Their instruments are open-source, their networks casual and their reputations constructed on credibility earned in public.
The night time shift crypto detectives
The trade’s most acknowledged blockchain sleuth is ZachXBT. He’s constructed a popularity for exact onchain forensics cited by authorities our bodies and investigations which have led to arrests.
Elsewhere within the ecosystem, a military of veteran researchers and self-taught hobbyists are doing comparable work within the digital shadows. One among them is 0xSaiyanGod, a safety researcher who constructed a bot to detect malicious websites and spent years tracing drainer teams.
“I introduce myself as a legendary Tremendous Saiyan, Prince of all Saiyans — or different loopy nicknames — however I’m 0xSaiyanGod,” he tells Journal. “Most individuals simply name me Saiyan.”
Saiyan works below a pseudonym however he repeatedly emphasised the significance of sharing credit score with the groups he works with. He requested that his interview with Journal be carried out with the video turned off citing safety considerations.
Like a lot of his friends, Saiyan has a life outdoors the display. He works an everyday job by day and hunts crypto scams by night time below his digital alias.
“I nonetheless have a nine-to-five. Then I come house, open Telegram, verify the reviews and begin tracing wallets. It’s the identical rhythm each night time,” he says.
He started as a bug bounty hunter within the Web2 scene and introduced that skillset into crypto safety in 2022. Early on, he tracked SIM-swapping phishing campaigns and the social engineering ways behind pockets drainer operations with teams akin to Pockets Guard and the safety collective BlockMage.
One of many key instances he labored on was the Blur browser extension rip-off with researcher NFT_Dreww — the place Inferno Drainer tricked victims into putting in a malicious add-on.
Saiyan’s first encounter with drainer exercise was throughout the interval when Monkey Drainer–type phishing kits have been spreading throughout Telegram. Saiyan mapped the infrastructure behind such campaigns, together with reused phishing templates, shared internet hosting setups and recurring wallet-chaining patterns. His work has since expanded to successor clusters related to Inferno Drainer, the place small code overlaps helped researchers flag new phishing domains.
Learn additionally
Options
Unlocking Cultural Markets with Blockchain: Web3 Manufacturers and the Decentralized Renaissance
Options
Crypto, Meet Fiat. You Two Ought to Get A Espresso Someday
To scale detection, he constructed Doom Bot, a Discord-based phishing and drainer detection bot that flagged suspicious hyperlinks and forwarded them into personal channels. Doom Bot and its friends have been early movers within the house earlier than bigger groups akin to SEAL took on that perform.
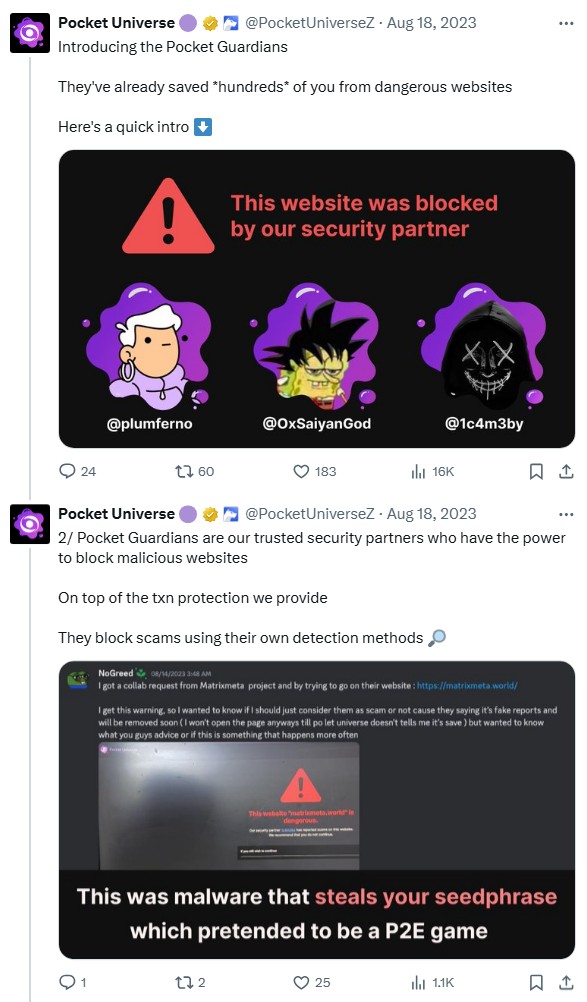
“The intel supplied to these groups at the moment was undoubtedly useful,” Saiyan says.
“I can reference one instrument of my buddy that was — perhaps nonetheless — doing the identical and reporting to Pocket Universe. Between us, we may catch most hyperlinks and supply the intel to groups.”
The tracing work that follows continues to be guide. Saiyan took half in figuring out and flagging wallets tied to North Korean–linked exercise throughout the $1.5 billion Bybit incident, publicly marking addresses on Etherscan. He makes use of tooling akin to blockchain explorers, Arkham, MetaSleuth and Breadcrumbs. Excessive-end forensics platforms like Chainalysis are sometimes reserved for regulation enforcement and institutional groups.
The human aspect of crypto investigations
Whereas most crypto detectives use pseudonyms, Heiner Garcia doesn’t. A former safety analyst for Colombia’s Ministry of Protection, he spent years in human intelligence operations tied to felony networks earlier than becoming a member of Telefónica’s safety division.
“I’ve handled actual threat,” he says. “Narcos, corrupt politicians, troopers, police — the form of work the place you truly conceal as a result of somebody may kill you.”
That have formed how he views the web menace panorama.
“The true hazard isn’t right here, behind a pc,” he says. “If I get doxxed on-line, advantageous. But when I get doxxed on the market, I’d get killed.”
Learn additionally
Options
I turned an Ordinals RBF sniper to get wealthy… however I misplaced most of my Bitcoin
Options
Blockchain fail-safes in house: SpaceChain, Blockstream and Cryptosat
His investigations rely closely on human intelligence ideas — studying context, finding out conduct and mixing into digital environments.
“Every thing is context,” he says. “If you wish to perceive a goal, you need to perceive what’s round them — what they like, how they join, the instruments they use.”
⚡️ INSIGHT: A North Korean crypto spy pretending to be a Japanese crypto dev walked right into a pretend job interview arrange by safety researcher Heiner Garcia. Cointelegraph was invited to attend undercover. By the top, he rage-quit and left behind a path of breadcrumbs. pic.twitter.com/pZ6F11ElfL
— Cointelegraph (@Cointelegraph) Could 7, 2025
Garcia builds pretend profiles that mirror the builders or hackers he research. He will get so near his targets that a few of them even comply with his pretend profiles.
Throughout the crypto safety group, Garcia has constructed a popularity for profiling and even interacting with suspected North Korean IT staff. “If I see 5 completely different profiles utilizing the identical avatar, identical code patterns and the identical repositories, I do know it’s coordinated,” he says.
In a single case, he traced a cluster of North Korean builders by posing as a collaborator on open-source initiatives.
“They thought I used to be considered one of them,” he says. “I noticed how they recruit others, how they convey, what instruments they use to maneuver cash. It’s human intelligence, not cyber forensics.”
Garcia’s strategy, which blends OSINT with HUMINT, reveals behavioral patterns that automated instruments usually miss.
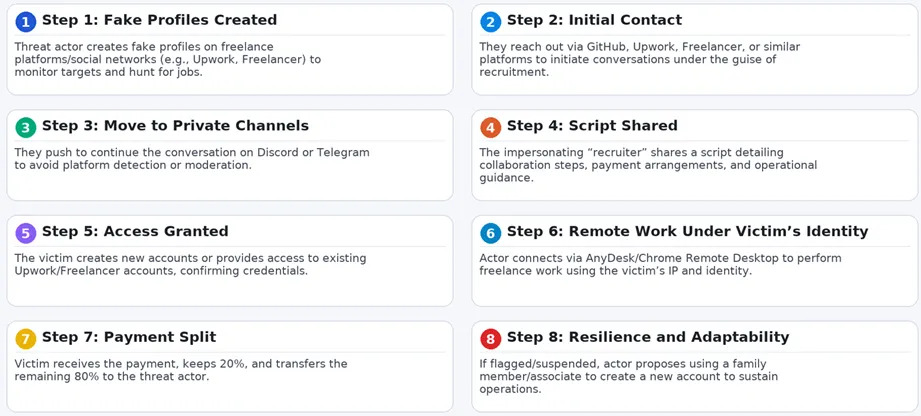
“In case you solely have a look at IPs and malware, you’re chasing ghosts,” he says. “However should you perceive the folks — their motives [and] their routines — you begin seeing the construction behind the operations.”
Inside a crypto incident response conflict room
When a hack breaks out, intelligence work shifts from routine monitoring to disaster response. Throughout the blockchain safety world, the primary transfer is to open a channel for collaboration
“The second an incident begins, we open a conflict room,” Cos, founding father of safety firm SlowMist, tells Journal via a Mandarin interpreter. “The objective is to hint, include and alert as quick as potential.”
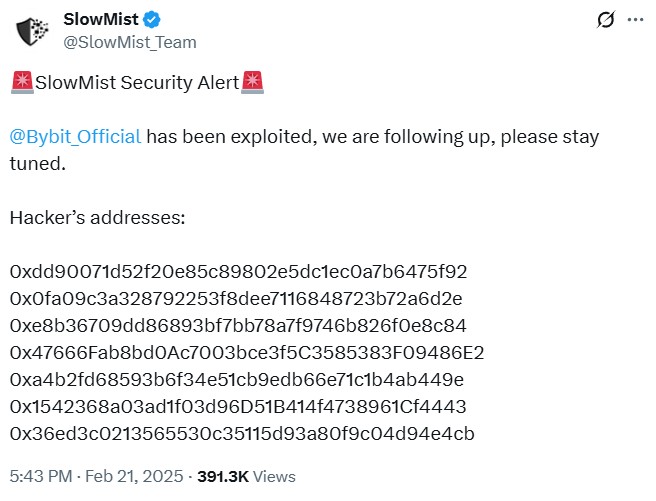
It begins off as an invite-only channel with trusted responders. Because the incident develops, extra events — akin to exchanges, companions and victims — be part of the conflict room. Even representatives from regulation enforcement businesses enter the chat.
Communication is tightly managed. Victims are sometimes requested to ship their public statements or screenshots to the group earlier than posting them, so delicate particulars don’t leak mid-operation.
Legislation enforcement often joins after the preliminary tracing work is underway.
“We have to transfer first,” Cos explains. “Legislation enforcement strikes slower. They want proof; we want velocity.”
Behind the scenes, SlowMist’s inside tooling helps all of this. MistTrack is used for pockets tracing and transaction visualization, whereas MistEye scans for malicious domains, phishing infrastructure, and contract-level exploits.
Learn additionally
Options
Bitcoin payday? Crypto to revolutionize job wages… or not
Options
Bitcoin ETFs make Coinbase a ‘honeypot’ for hackers and governments: Trezor CEO
Crypto safety wants reinforcements
The broader crypto safety group continues to be understaffed as hacks get bigger and laundering paths develop extra advanced, whereas the variety of skilled defenders has not stored tempo. Many main incidents are nonetheless first flagged by unbiased volunteers.
“There are all the time new assaults. Each week one thing occurs. There are usually not sufficient folks in safety, not sufficient analysts and never sufficient responders. We’d like extra individuals who can truly do the work,” Cos says.
Saiyan, who works safety on high of his full-time job, says these inquisitive about becoming a member of the sector want curiosity greater than credentials.
“You don’t have to be an knowledgeable from day one, you simply must look nearer than everybody else,” he says. “Hint each line and ask why one thing moved the way in which it did.”
In the meantime, Garcia advises future crypto sleuths to discover a area of interest.
“You may’t be good at all the pieces. Discover the area of interest you’re keen on, examine the context round it and do one thing excellent,” Garcia says.
Paths into the sector fluctuate. Some like Saiyan come from bug bounty circles and self-taught scripting. Others, like Garcia, arrive with navy or intelligence backgrounds. Firms like SlowMist mix structured response frameworks with open-source instincts. What unites them is the impulse to guard an trade value $3.5 trillion.
For Cos, the core problem is moral. His X deal with, @evilcos, serves as a reminder of precisely the place he stands, as a result of on this discipline, the talents used to defend techniques can simply as simply be used to use them.
“It’s a must to resolve what sort of particular person you wish to be,” he says. “You see some huge cash on this work and the road between good and unhealthy can get blurry. Don’t be evil.”
Subscribe
Essentially the most participating reads in blockchain. Delivered as soon as a
week.

Yohan Yun
Yohan Yun is a multimedia journalist overlaying blockchain since 2017. He has contributed to crypto media outlet Forkast as an editor and has lined Asian tech tales as an assistant reporter for Bloomberg BNA and Forbes. He spends his free time cooking, and experimenting with new recipes.
